 Kamis, 27 Februari 2025 (08:07)
Kamis, 27 Februari 2025 (08:07)
 Music |
 Video |
 Movies |
 Chart |
 Show |
 |
Metasploit For Beginners - How To Scan And Pwn A Computer | Learn From A Pro Hacker (Loi Liang Yang) View |
 |
Nmap Tutorial to find Network Vulnerabilities (NetworkChuck) View |
 |
How Hackers Scan Devices on a Network with Nmap | Kali Linux (HackHunt) View |
 |
Nmap scan using metasploit (hack in) View |
 |
METASPLOIT - HOW TO SCAN AND EXPLOIT A TARGET (Guyo Wario ) View |
 |
Metasploit Framework Series - Metasploit with Nmap Scanning - Part 1 (Motasem Hamdan | Cyber Security \u0026 Tech) View |
 |
Metasploit - 07 - db nmap scan (Learn IT (Know IT)) View |
 |
Import Nmap scan result into Metasploit / Using Nmap with Metasploit (AGStorm) View |
 |
CEH v13 Module 4 | System Hacking with Metasploit u0026 Nmap | Ethical Hacking #ethicalhacking (Senseacademy) View |
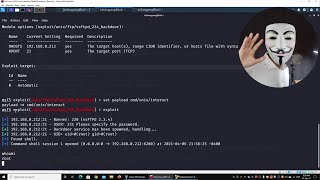 |
Metasploit Tutorial for Beginners (Loi Liang Yang) View |