 Rabu, 5 Maret 2025 (18:12)
Rabu, 5 Maret 2025 (18:12)
 Music |
 Video |
 Movies |
 Chart |
 Show |
 |
Proxy Re-encryption Explained (IronCore Labs) View |
 |
Proxy Re-encryption (Transformation Encryption) (Bill Buchanan OBE) View |
 |
Proxy re-encryption with Michael Egorov (Pentester Academy TV) View |
 |
Proxy In 5 Minutes | What Is A Proxy | What Is A Proxy Server | Proxy Explained | Simplilearn (Simplilearn) View |
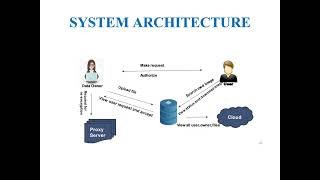 |
Proxy re encryption for secure medical data sharing in cloud (Niresh Suresh) View |
 |
Transform Crypto Overview (IronCore Labs) View |
 |
22 Proxy Re encryption in Access Control framework of information centric networks (Engineering CSE Projects) View |
 |
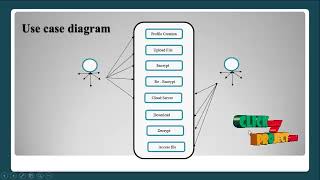
USENIX Security '21 - Reducing HSM Reliance in Payments through Proxy Re-Encryption (USENIX) View |
 |
A Pre-Authentication Approach to Proxy Re-encryption in Big Data Context (ClickMyProject) View |
 |
A secure cloud server system using proxy Re Encryption Model | 1 Crore projects (1Crore Projects) View |